#
Our Google Cloud Permissions in Your Environment
When you set up Retail Cloud Connect for the first time, you will be asked to grant the application access to one or more Google Cloud projects when configuring your cloud connection.
In the interest of security and transparency, this FAQ page explains exactly what permissions Retail Cloud Connect uses and why it uses them.
Contact Us
Please contact us if you have additional security-related questions.
#
Service Account
When you create a Retail Cloud Connect retailer, a unique Service Account is provisioned in Nimstrata's Google Cloud organization so you customers don't need to manage additional keys or credentials.
Service Accounts enable computers to talk to each other securely without the need to share user passwords. Because Nimstrata owns this Service Account, it can only access your Google Cloud environment if you give it permission to do so. Not only does this give you full control over your data security, it’s also very easy to remove Retail Cloud Connect's access if you decide to use a different solution.
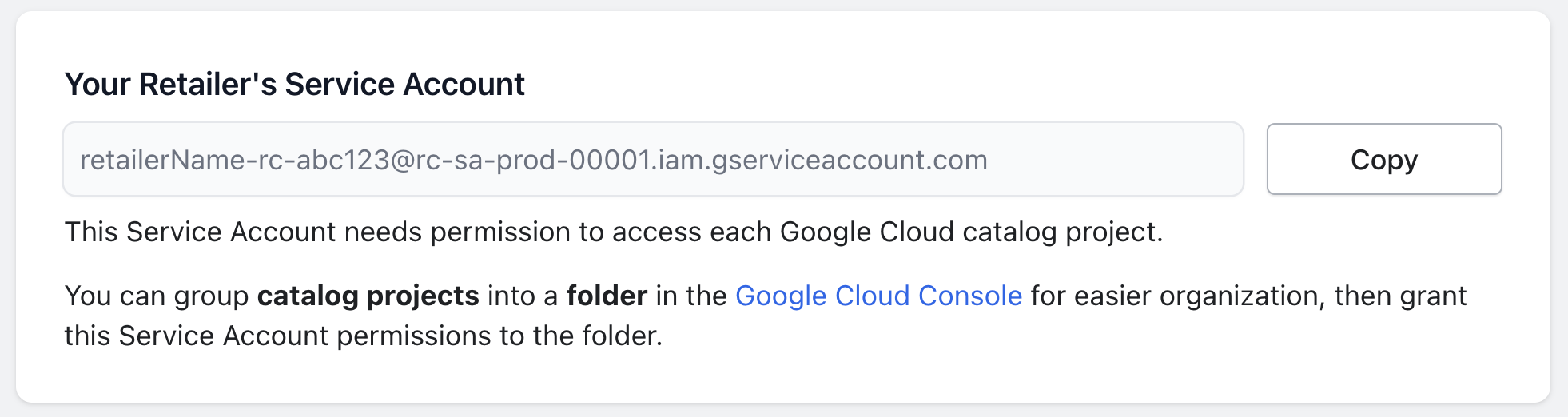
You can see your full Service Account email address in the Retail Cloud Connect dashboard, it will look similar to this:
#
Required Permissions
Retail Cloud Connect requires several permissions to properly administer your Google Cloud retail catalog project. The permissions are included in two roles. Google Cloud IAM roles are a set of one or more permissions.
#
Retail Cloud Connect Custom Role
First, we guide you through creating a Custom Role in your Google Cloud environment that grants our application permission to view the project that your retail catalog belongs to:
gcloud iam roles create retail_cloud_connect \\
--project="your-catalog" \\
--title="Permissions for Retail Cloud Connect via Shopify" \\
--description="Allows Retail Cloud Connect to manage Google Cloud Retail API" \\
--permissions=resourcemanager.projects.get,serviceusage.services.list
gcloud projects add-iam-policy-binding your-catalog \\
--member=serviceAccount:your-sa@rc-sa-prod-00001.iam.gserviceaccount.com \\
--role=projects/your-catalog/roles/retail_cloud_connectNimstrata follows a data security best practice known as the principle of least privilege, by using a Custom Role to ensure that we don’t have any unnecessary privileges in your environment.
#
Retail Admin Role
The Retail Admin role contains a set of permissions that allows us to fully manage your catalog data. While you can grant the Retail Editor role instead, our tooling will not be able to purge catalogs which may be a necessary step when performing imports with new schemas.
gcloud projects add-iam-policy-binding your-catalog \\
--member=serviceAccount:your-sa@rc-sa-prod-00001.iam.gserviceaccount.com \\
--role=roles/retail.admin
#
Google Cloud Project
We recommend using a single-purpose Google Cloud project for your retail catalog data. This allows you to provide tightly scoped access to Retail Cloud Connect and remove cross-configuration risk around other resources inside of Google Cloud.
For example, if you have an existing Google Cloud project with other resources in it such as your Google Analytics data in BigQuery or virtual machines running your ERP, other administrators inside of your company may accidentally alter or delete your retail catalog data.
If you’re a new Google Cloud user, this should not be a concern.
#
Removing Permissions
Please only remove permissions with a contingency plan and caution!
If you remove our app's permissions, Retail Cloud Connect will no longer be able to update your catalog or serve search results or recommendations on your website.
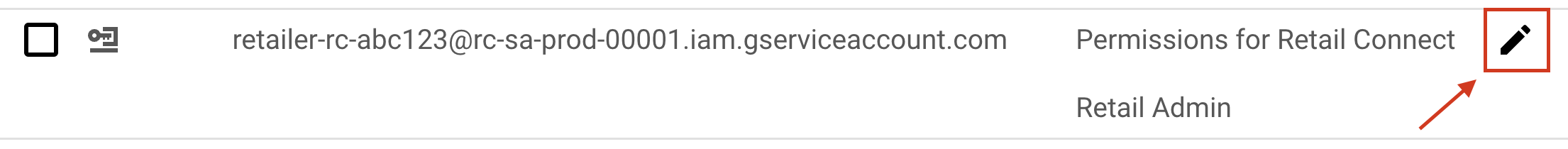
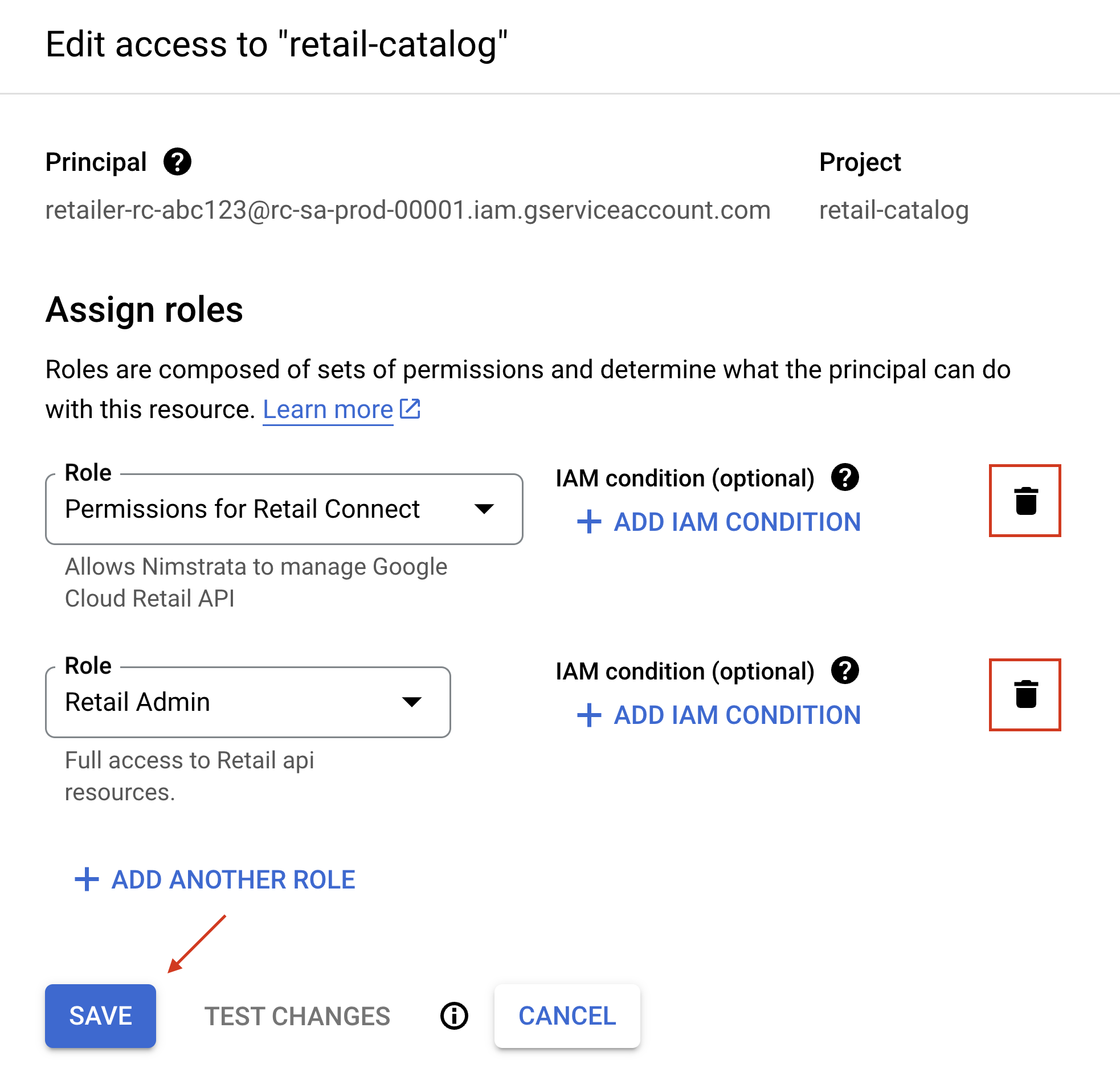
To remove Retail Cloud Connect’s access to your Google Cloud project:
- Visit the Google Cloud IAM page for your retail catalog project
- Click the Service Account edit (pencil) icon
- Remove the two roles with the delete (trashcan) icon
- Click the Save button
#
Further Reading
For advanced explanations of each role's permissions, review the following Google Cloud documentation: